MISC
签到
flag:XYCTF{WELCOME_TO_XYCTF}
关注公众号回复
game
flag:XYCTF{Papers Please}
谷歌识图游戏名
熊博士
flag:XYCTF{liu_ye_mei_you_xiao_jj}
解出小纸条转为atbash码是xyctf{liu_ye_mei_you_xiao_jj},根据提示flag头大写,改为大写即可
jpg查到有jphide隐写,但是密码未知,纯nt设计
ez_隐写
flag:XYCTF{159-WSX-IJN-852}
压缩包伪加密,先去除伪加密
得到一个hint.png和加密压缩包
png修复宽高,得到提示:开赛日期
即压缩包密码是20240401,解压得到一个watermark.jpg,用盲水印工具提取,瞪眼法得到flag
ZIP神之套
flag:XYCTF{1A4B8-C9D2F3E-6A4B8C-9D2F3E7F}
zip文件,第一层是exe和一个加密zip,exe运行出xyctf????????ftcyx,推测掩码攻击,得到密码xyctf20240401ftcyx
解压出两个压缩包,一个加密一个未加密,未加密里有加密压缩包里的文件,推测明文攻击,得到flag.md,搜索XYCTF得到flag
TCPL
flag:FLAG{PLCT_An4_r0SCv_x0huann0}
ELF文件,但是不能直接运行,怀疑文件被修改
ida分析可以看到数据段,根据题目描述flag开头是FLAG{
直接用ida读汇编语言,这里待完善
首先是异或
cipher = [ '444A557F44434D46' , '3E7C5238654B565C' , '627E246C4C645243' , '2A747779' , '61' ]
text = []
for i in cipher :
for j in range ( len ( i ) - 1 , -1 , -2 ) :
text.append ( int ( i [ j - 1 : j + 1 ] , 16 ) )
for i in range ( len ( text ) ) :
print ( chr ( text [ i ] ^ i ) , end = '')
FLAG{TCPL_An4_r1SCv_x1huann1}
然后输出了一个图形,让其中的1变成这个图形,推断出是0
***
* *
* *
***
zzl的护理小课堂
flag:XYCTF{2zL_tEII_you_915a36eb7a38}
web题,burpsuite抓包修改响应,使其提交时直接输出flag即可
真>签到
flag:XYCTF{59bd0e77d13c_1406b23219e_f91cf3a_153e8ea4_77508ba}
zip加密压缩包,但是010editor打开在文件头就发现了flag
Rosk,Paper,Scissors!
flag:XYCTF{ROSk,PapeR,SclsS0R5_01581dd30576}
靶机交互题,与程序进行石头剪刀布,第一次完全随机,后面的99次取决于之前的猜拳情况,根据程序逻辑反推出解即可
这里socket一直连接不上,改用pwntool连接
from pwn import *
from pwn import p64 , p32
from collections import Counter
import random
palyerinputs = []
def most_common_element(arr):
counter = Counter(arr)
most_common = counter.most_common(1)
return most_common[0][0] if most_common else None
def random_ai(palyerinputs):
seed = palyerinputs[:-1]
if len(seed) == 0:
return random.randint(1, 3)
else:
return (most_common_element(seed) - 2) % 3 + 1
IP = '127.0.0.1'
port = 7052
s = remote ( IP , port )
print ( s.recv().decode() )
palyerinputs.append ( 1 )
s.sendline ( b'Rock' )
print ( s.recv().decode() )
cnt = 0
while cnt != 100 :
for i in range ( 1 , 4 ) :
palyerinputs.append ( i )
aiinput = random_ai(palyerinputs)
if ( i == 1 and aiinput != 2 ) or ( i == 2 and aiinput != 3 ) or ( i == 3 and aiinput != 1 ) :
palyerinputs.pop ( )
continue
if aiinput == 1 :
s.sendline ( b'Scissors' )
break
elif aiinput == 2 :
s.sendline ( b'Rock' )
break
elif aiinput == 3 :
s.sendline ( b'Paper' )
break
print ( s.recv().decode() )
cnt += 1
print ( s.recvall().decode() )
Osint1
flag:xyctf{江苏省|南通市|滨海东路|黄海}
小红书识图
EZ_Base1024*2
flag:XYCTF{84ca3a6e-3508-4e34-a5e0-7d0f03084181}
base2048
CRYPTO
Sign1n[签到]
flag:XYCTF{e883e6eb-f8e2-478a-a92d-fff024cc9de6}
将flag转为长整形,然后转为二进制字符串,补全为514位,末尾补零,翻转后再进行加法模运算。逆向即可
from Crypto.Util.number import long_to_bytes
# 给定的加密后的字符串 b
b = "12345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567891134567780113445779902334577801133467889122346779001245567991223466790012345788902334677801124556899023355788001235568990223566799023445778902335578800133456899012456679011344567991223557880012445788911334677890234456899023355788001244568991133467780113445779902335667900123467889012456679911245578801233467789112355779912234577990233556780113"
# 逆自定义加法
def reverse_custom_add(input_str):
input_list = list(input_str)
length = len(input_list)
for i in range(length):
input_list[i] = str((int(input_list[i]) - i - 1 + 10) % 10)
result = ''.join(input_list)
return result
# 逆位翻转
def reverse_swap_bits(input_str):
input_list = list(input_str)
length = len(input_list)
for i in range(length // 2):
temp = input_list[i]
input_list[i] = input_list[length - 1 - i]
input_list[length - 1 - i] = temp
return ''.join(input_list)
# 执行逆变换
reversed_b = reverse_custom_add(b)
reversed_leak = reverse_swap_bits(reversed_b)
# 移除添加的零
original_leak = reversed_leak.rstrip('0')
# 二进制到整数的转换
original_flag_int = int(original_leak, 2)
# 整数到字节串的转换
original_flag = long_to_bytes(original_flag_int)
print ( original_flag )
Sign1n_Revenge
flag:flag{707a37ba-c623-449d-bebe-9a92728f940a}
同上,只需连接上靶机得到附件的密文即可
REVERSE
聪明的信使
flag:flag{Y0u_KnOw_Crypt0_14_v3ry_Imp0rt@nt!}
凯撒加密,key=9
喵喵喵的flag碎了一地
flag:flag{My_fl@g_h4s_br0ken_4parT_Bu7_Y0u_c@n_f1x_1t!}
根据题目提示,flag分为三部分
- 第一部分,string搜索 flag{My_fl@g_
- 第二部分,函数名搜索 h4s_br0ken_4parT_
- 第三部分,第二部分的函数名引用,分为两块,第一块在putchar Bu7_Y0u_c@n_,第二块在汇编代码里 f1x_1t!}
你是真的大学生吗?
flag:xyctf{you_know_8086}
asm逆向,字符串异或
cipher = [0x76, 0x0E, 0x77, 0x14, 0x60, 0x06, 0x7D, 0x04, 0x6B, 0x1E, 0x41, 0x2A, 0x44, 0x2B, 0x5C, 0x03, 0x3B, 0x0B, 0x33, 0x05]
for i in range ( len ( cipher ) - 1 ) :
cipher [ i ] = cipher [ i ] ^ cipher [ i + 1 ]
for i in range ( len ( cipher ) ) :
print ( chr ( cipher [ i ] ), end = "" )
ez_cube
flag:flag{RuRURURururr}
魔方题,给出一个待还原的魔方,需要还原,这里先分析出魔方的结构
for ( i = 0; i < 9; ++i )
{
zhengmian[i] = "Red";
zuobian[i] = "Blue";
youmian[i] = "Green";
houmian[i] = "Orange";
shangmian[i] = "Yellow";
xiamian[i] = "White";
}
zuobian[1] = "Red";
zhengmian[1] = "Green";
youmian[1] = "Blue";
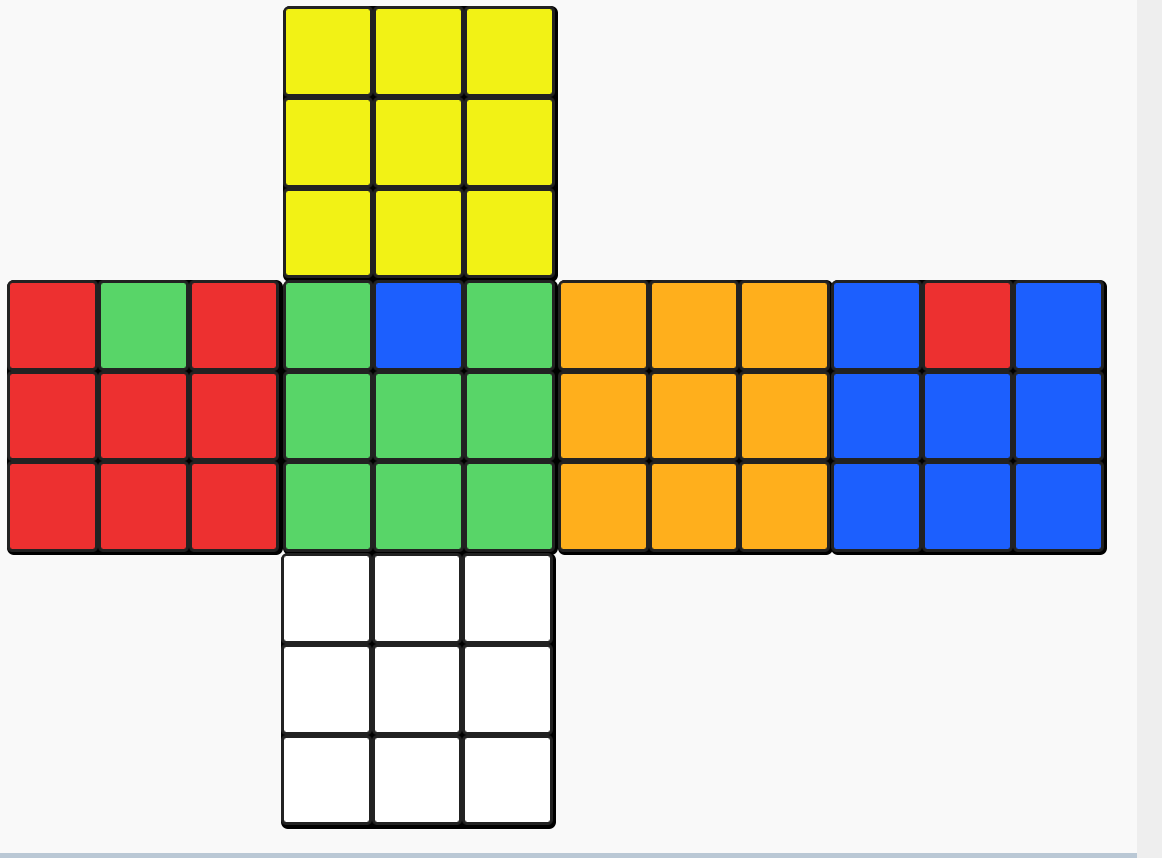
然后可以知道,程序只允许R、U、r、u四种操作方法
这个是最基础的还原操作,刚好十二步
RuRURURururr,得到flag
给阿姨倒一杯卡布奇诺
flag:XYCTF{133bffe401d223a02385d90c5f1ca377}
魔改tea,脚本按照逻辑解密即可
#include <bits/stdc++.h>
using namespace std ;
void encrypt (uint32_t* v, uint32_t* k) {
uint32_t v0 = v[0], v1 = v[1], sum = 0;
uint32_t delta = 1853174124 ;
sum = delta * 32 ;
for ( int i = 31; i >= 0 ; i--) {
v1 -= ((v0<<4) + k[2]) ^ (v0 + sum) ^ ((v0>>5) + k[3]) ^ ( sum + i ) ; // sum + i 魔改
v0 -= ((v1<<4) + k[0]) ^ (v1 + sum) ^ ((v1>>5) + k[1]) ^ ( sum + i ) ;
sum -= delta;
}
v[0] = v0;
v[1] = v1;
}
int main() {
uint32_t k[4] = {1702259047, 1970239839, 1886741343, 1634038879};
int32_t input[8] = {0x9B28ED45,0x145EC6E9,0x5B27A6C3,0xE59E75D5,0xE82C2500,0xA4211D92,0xCD8A4B62,0xA668F440};
//scanf("%32s", input);
uint32_t data1 = 0x5F797274 , data2 = 0x64726168 ;
for (int i = 0; i < 8; i+=2) {
uint32_t v[2] = {*(uint32_t *)&input[i], *(uint32_t *)&input[i+1]} ;
encrypt(v, k);
v [ 0 ] ^= data1 , v [ 1 ] ^= data2 ; //异或魔改
data1 = input [ i ] , data2 = input [ i + 1 ] ;
for (int j = 0; j < 2; j++) {
for (int k = 0; k < 4; k++) {
printf("%c", v[j] & 0xff);
v[j] >>= 8;
}
}
}
return 0;
}
ez_rand
flag:XYCTF{R@nd_1s_S0_S0_S0_easy!}
时间戳爆破题,需要先爆出时间戳,由于给定flag格式为XYCTF{,所以可以根据这个来爆破
#include <bits/stdc++.h>
using namespace std ;
int main() {
for ( register int i = 0 ; i <= 1000000000000 ; ++i ) {
srand ( i ) ;
int v7 = rand ( ) ;
if ( (unsigned __int8)(v7 + ((((unsigned __int64)(2155905153 * v7) >> 32) & 0x80000000 ) != 0) + ((int)((unsigned __int64)(2155905153 * v7) >> 32) >> 7)) == 5 ) {
v7 = rand ( ) ;
if ( (unsigned __int8)(v7 + ((((unsigned __int64)(2155905153 * v7) >> 32) & 0x80000000 ) != 0) + ((int)((unsigned __int64)(2155905153 * v7) >> 32) >> 7)) == 85 ) {
v7 = rand ( ) ;
if ( (unsigned __int8)(v7 + ((((unsigned __int64)(2155905153 * v7) >> 32) & 0x80000000 ) != 0) + ((int)((unsigned __int64)(2155905153 * v7) >> 32) >> 7)) == 47 ) {
v7 = rand ( ) ;
if ( (unsigned __int8)(v7 + ((((unsigned __int64)(2155905153 * v7) >> 32) & 0x80000000 ) != 0) + ((int)((unsigned __int64)(2155905153 * v7) >> 32) >> 7)) == 190 ) {
v7 = rand ( ) ;
if ( (unsigned __int8)(v7 + ((((unsigned __int64)(2155905153 * v7) >> 32) & 0x80000000 ) != 0) + ((int)((unsigned __int64)(2155905153 * v7) >> 32) >> 7)) == 0 ) {
cout << i << " " ;
}
}
}
}
}
}
return 0;
}
得到种子21308
根据种子进行解密即可
#include <bits/stdc++.h>
using namespace std ;
int data[29] = {
0x5D, 0x0C, 0x6C, 0xEA, 0x46, 0x19, 0xFC, 0x34, 0xB2, 0x62, 0x23, 0x07, 0x62, 0x22, 0x6E, 0xFB,
0xB4, 0xE8, 0xF2, 0xA9, 0x91, 0x12, 0x21, 0x86, 0xDB, 0x8E, 0xE9, 0x43 ,0x4d
};
int main ( ) {
srand ( 21308 ) ;
for ( int i = 0 ; i < 29 ; ++i ) {
int v7 = rand ( ) ;
data [ i ] ^= (unsigned __int8)(v7 + ((((unsigned __int64)(2155905153 * v7) >> 32) & 0x80000000 ) != 0) + ((int)((unsigned __int64)(2155905153 * v7) >> 32) >> 7)) ;
}
for ( int i = 0 ; i < 29 ; ++i ) {
cout << char ( data [ i ] ) ;
}
return 0 ;
}
砸核桃
flag:flag{59b8ed8f-af22-11e7-bb4a-3cf862d1ee75}
手脱壳例题,脱开就能看到flag的异或逻辑,编写脚本解密
key = 'this_is_not_flag'
cipher = [0x12, 0x00, 0x00, 0x00, 0x04, 0x00, 0x00, 0x00, 0x08, 0x00, 0x00, 0x00, 0x14, 0x00, 0x00, 0x00, 0x24, 0x00, 0x00, 0x00, 0x5C, 0x00, 0x00, 0x00, 0x4A, 0x00, 0x00, 0x00, 0x3D, 0x00, 0x00, 0x00, 0x56, 0x00, 0x00, 0x00, 0x0A, 0x00, 0x00, 0x00, 0x10, 0x00, 0x00, 0x00, 0x67, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x41, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x46, 0x00, 0x00, 0x00, 0x5A, 0x00, 0x00, 0x00, 0x44, 0x00, 0x00, 0x00, 0x42, 0x00, 0x00, 0x00, 0x6E, 0x00, 0x00, 0x00, 0x0C, 0x00, 0x00, 0x00, 0x44, 0x00, 0x00, 0x00, 0x72, 0x00, 0x00, 0x00, 0x0C, 0x00, 0x00, 0x00, 0x0D, 0x00, 0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x3E, 0x00, 0x00, 0x00, 0x4B, 0x00, 0x00, 0x00, 0x5F, 0x00, 0x00, 0x00, 0x02, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x4C, 0x00, 0x00, 0x00, 0x5E, 0x00, 0x00, 0x00, 0x5B, 0x00, 0x00, 0x00, 0x17, 0x00, 0x00, 0x00, 0x6E, 0x00, 0x00, 0x00, 0x0C, 0x00, 0x00, 0x00, 0x16, 0x00, 0x00, 0x00, 0x68, 0x00, 0x00, 0x00, 0x5B, 0x00, 0x00, 0x00, 0x12, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x48, 0x00, 0x00, 0x00]
for i in range ( 42 ) :
print ( chr ( cipher [ i * 4 ] ^ ord ( key [ i % 16 ] ) ) , end = '' )
ez_enc
flag:flag{!r3ea11y_w4nt@_cu7e_s1$ter}
逻辑分析
for ( i = 0; i < (int)(j_strlen(Str) - 1); ++i )
Str[i] = aImouto[i % 6] ^ (Str[i + 1] + (unsigned __int8)Str[i] % 20);
for ( j = 0; j < (int)j_strlen(Str); ++j )
{
if ( Str[j] != byte_14001E008[j] )
{
sub_1400111A4("Wrong");
return 0;
}
}
这里的核心逻辑是Str[i] = aImouto[i % 6] ^ (Str[i + 1] + (unsigned __int8)Str[i] % 20);
很容易想到dfs倒推,约束条件是前五个字符为flag{,但是没有成功,遂发现了正推的逻辑,脚本实现
只要推出了第一个是f,就很好做了,可以挨个进行递推
cipher = [0x27, 0x24, 0x17, 0x0B, 0x50, 0x03, 0xC8, 0x0C, 0x1F, 0x17, 0x36, 0x55, 0xCB, 0x2D, 0xE9, 0x32, 0x0E, 0x11, 0x26, 0x02, 0x0C, 0x07, 0xFC, 0x27, 0x3D, 0x2D, 0xED, 0x35, 0x59, 0xEB, 0x3C, 0x3E, 0xE4, 0x7D]
key = 'IMouto'
flag = []
flag.append ( 'f' )
for i in range ( len ( cipher ) - 1 ) :
flag.append ( chr ( ( cipher [ i ] ^ ord(key [ i % 6 ]) ) - ord ( flag [ i ] ) % 20 ) )
for i in flag :
print ( i , end = '' )
ezmath
flag:XYCTF{q7WYGscUuptTYXjnjKoyUTKtG}
py打包的exe,解包后反编译pyc文件,得到一大串的判断flag语句,拆开分析,主要是两种
sum([flag[i] for _ in range(flag[i])])
sum([flag[i] for _ in range(m)])
容易发现,flag[31]对应最后一个字符,而此处的m为250,正好是125的两倍
查看前五个字符,也正好是XYCTF的两倍,所以提取出来,即可得到flag
import re
with open('D:/桌面/1.txt', 'r') as file:
lines = file.readlines()
# 准备输出的代码
output_code = []
# 正则表达式,用于提取flag索引和范围
pattern = re.compile(r"flag\[(\d+)\] for _ in range\((\d+)\)")
for line in lines:
# 使用正则表达式匹配行
match = pattern.search(line)
if match:
# 提取flag的索引和重复次数
index = match.group(1)
count = match.group(2)
# 创建新的代码行
new_line = f"flag[{index}] = {count} // 2\n"
output_code.append(new_line)
# 将生成的代码写入输出文件
for i in output_code :
print ( i )
flag = [0] * 32
flag[24] = 222 // 2
flag[9] = 178 // 2
flag[29] = 232 // 2
flag[23] = 150 // 2
flag[6] = 226 // 2
flag[7] = 110 // 2
flag[0] = 176 // 2
flag[12] = 198 // 2
flag[3] = 168 // 2
flag[2] = 134 // 2
flag[13] = 170 // 2
flag[10] = 142 // 2
flag[15] = 224 // 2
flag[11] = 230 // 2
flag[1] = 178 // 2
flag[5] = 246 // 2
flag[17] = 168 // 2
flag[21] = 220 // 2
flag[22] = 212 // 2
flag[16] = 232 // 2
flag[4] = 140 // 2
flag[31] = 250 // 2
flag[28] = 150 // 2
flag[14] = 234 // 2
flag[8] = 174 // 2
flag[25] = 242 // 2
flag[30] = 142 // 2
flag[26] = 170 // 2
flag[19] = 176 // 2
flag[27] = 168 // 2
flag[20] = 212 // 2
flag[18] = 178 // 2
for i in flag :
print ( chr ( i ) , end = '' )
何须相思煮余年
flag:XYCTF{5b3e07567a9034d06851475481507a75}
给了字节码,用ida打开一个新的00程序,先覆盖patch进去
import ida_bytes
def simulate_xor_encryption(start_addr, size):
modified_data = [0x55,0x8b,0xec,0x81,0xec,0xa8,0x0,0x0,0x0,0xa1,0x0,0x40,0x41,0x0,0x33,0xc5,0x89,0x45,0xfc,0x68,0x9c,0x0,0x0,0x0,0x6a,0x0,0x8d,0x85,0x60,0xff,0xff,0xff,0x50,0xe8,0x7a,0xc,0x0,0x0,0x83,0xc4,0xc,0xc7,0x85,0x58,0xff,0xff,0xff,0x27,0x0,0x0,0x0,0xc7,0x85,0x5c,0xff,0xff,0xff,0x0,0x0,0x0,0x0,0xeb,0xf,0x8b,0x8d,0x5c,0xff,0xff,0xff,0x83,0xc1,0x1,0x89,0x8d,0x5c,0xff,0xff,0xff,0x83,0xbd,0x5c,0xff,0xff,0xff,0x27,0xf,0x8d,0xed,0x0,0x0,0x0,0x8b,0x95,0x5c,0xff,0xff,0xff,0x81,0xe2,0x3,0x0,0x0,0x80,0x79,0x5,0x4a,0x83,0xca,0xfc,0x42,0x85,0xd2,0x75,0x25,0x8b,0x85,0x5c,0xff,0xff,0xff,0x8b,0x8c,0x85,0x60,0xff,0xff,0xff,0x3,0x8d,0x5c,0xff,0xff,0xff,0x8b,0x95,0x5c,0xff,0xff,0xff,0x89,0x8c,0x95,0x60,0xff,0xff,0xff,0xe9,0xac,0x0,0x0,0x0,0x8b,0x85,0x5c,0xff,0xff,0xff,0x25,0x3,0x0,0x0,0x80,0x79,0x5,0x48,0x83,0xc8,0xfc,0x40,0x83,0xf8,0x1,0x75,0x22,0x8b,0x8d,0x5c,0xff,0xff,0xff,0x8b,0x94,0x8d,0x60,0xff,0xff,0xff,0x2b,0x95,0x5c,0xff,0xff,0xff,0x8b,0x85,0x5c,0xff,0xff,0xff,0x89,0x94,0x85,0x60,0xff,0xff,0xff,0xeb,0x73,0x8b,0x8d,0x5c,0xff,0xff,0xff,0x81,0xe1,0x3,0x0,0x0,0x80,0x79,0x5,0x49,0x83,0xc9,0xfc,0x41,0x83,0xf9,0x2,0x75,0x23,0x8b,0x95,0x5c,0xff,0xff,0xff,0x8b,0x84,0x95,0x60,0xff,0xff,0xff,0xf,0xaf,0x85,0x5c,0xff,0xff,0xff,0x8b,0x8d,0x5c,0xff,0xff,0xff,0x89,0x84,0x8d,0x60,0xff,0xff,0xff,0xeb,0x38,0x8b,0x95,0x5c,0xff,0xff,0xff,0x81,0xe2,0x3,0x0,0x0,0x80,0x79,0x5,0x4a,0x83,0xca,0xfc,0x42,0x83,0xfa,0x3,0x75,0x20,0x8b,0x85,0x5c,0xff,0xff,0xff,0x8b,0x8c,0x85,0x60,0xff,0xff,0xff,0x33,0x8d,0x5c,0xff,0xff,0xff,0x8b,0x95,0x5c,0xff,0xff,0xff,0x89,0x8c,0x95,0x60,0xff,0xff,0xff,0xe9,0xf7,0xfe,0xff,0xff,0x33,0xc0,0x8b,0x4d,0xfc,0x33,0xcd,0xe8,0x4,0x0,0x0,0x0,0x8b,0xe5,0x5d,0xc3]
# 将修改后的数据转换为bytes对象后写回到相同的地址
if not ida_bytes.patch_bytes(start_addr, bytes(modified_data)):
print("Failed to patch bytes.")
else:
print("Encryption simulated successfully.")
# 脚本的入口点
if __name__ == "__main__":
# 函数起始位置
start_address = 0x00
# 数据大小,根据给定的循环次数决定
data_size = 344
# 执行加密模拟
simulate_xor_encryption(start_address, data_size )
然后查看汇编代码,用gpt分析或用ida分析
void function() {
int local_array[42]; // 假设数组大小为42,实际大小取决于A8h的解释
int i = 0;
for (; i < 39; i++) { // 假设循环到39,实际上是对'27h'的解释
int index = i & 3; // 实际上对应汇编中的 'and edx, 80000003h'
if (index == 0) {
local_array[i] += i;
} else if (index == 1) {
local_array[i] -= i;
} else if (index == 2) {
local_array[i] *= i;
} else if (index == 3) {
local_array[i] ^= i;
}
}
}
for ( i = 0; i < 39; ++i )
{
if ( i % 4 )
{
switch ( i % 4 )
{
case 1:
v2[i] -= i;
break;
case 2:
v2[i] *= i;
break;
case 3:
v2[i] ^= i;
break;
}
}
else
{
v2[i] += i;
}
}
根据逻辑逆向即可
enc = [88,88,134,87,74,118,318,101,59,92,480,60,65,41,770,110,73,31,918,39,120,27,1188,47,77,24,1352,44,81,23,1680,46,85,15,1870,66,91,16,4750]
flag = ''
for i in range ( len ( enc ) ) :
index = i & 3
if index == 0 :
enc [ i ] -= i
elif index == 1 :
enc [ i ] += i
elif index == 2 :
enc [ i ] //= i
else :
enc [ i ] ^= i
flag += chr ( enc [ i ] )
print ( flag )
What's this
flag:XYCTF{5dcbaed781363fbfb7d8647c1aee6c}
lua文件,先用unluac反编译
java -jar unluac_2023_11_15.jar what.lua > what_de.lua
得到源码,发现一堆反混淆,提取出关键代码
while true do
local temp = string.byte(flag, i)
temp = string.char(Xor(temp, 8) % 256)
value = value .. temp
i = i + 1
if i > string.len(flag) then
break
end
end
for i = 1, string.len(flag) do
temp = string.byte(value, i)
temp = string.char(temp + 3)
output = output .. temp
end
require("base64")
obfuscated_output = to_base64(output)
obfuscated_output = string.reverse(obfuscated_output)
obfuscated_output = string.gsub(obfuscated_output, "g", "3")
obfuscated_output = string.gsub(obfuscated_output, "H", "4")
obfuscated_output = string.gsub(obfuscated_output, "W", "6")
invalid_variable = obfuscated_output:rep(5)
if obfuscated_output == "==AeuFEcwxGPuJ0PBNzbC16ctFnPB5DPzI0bwx6bu9GQ2F1XOR1U" then
print("You get the flag.")
else
print("F**k!")
end
异或取模 -> 加法 -> base64 -> 字符串的反转替换
cipher = "STN_Qv@onmlpoB3<>A>qmqmBo3A?Bn<lppAnx"
for i in range ( len ( cipher ) ) :
a = chr ( ( ord ( cipher [ i ] ) - 3 ) ^ 8 )
print ( a , end = '' )
舔狗四部曲--简爱
flag:FLAG{vm_is_A_3ecreT_l0Ve_revers}
gra = [2,1,1,1,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,1,1,1,1,1,1,1,1,1,2,0,0,0,0,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,2,1,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,2,0,0,0,0,0,0,0,0,0,4,2,0,0,0,0,0,0,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,2,1,1,1,1,4,2,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,0,0,0,0,2,1,1,1,1,1,1,1,1,1,1,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,1,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,2,0,0,2,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,2,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,5,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,4,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,2,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,2]
cipher = 'flag{Love_is_not_one_sided_Love}'
ci = list ( cipher )
c = []
for i in range ( len ( ci ) ) :
c.append ( ord ( ci [ i ] ) )
flag = ''
dex = len ( c ) - 1
for i in gra :
if i == 2 :
dex -= 1
flag += chr ( c [ dex + 1 ] )
elif i == 1 :
c [ dex ] += 1
elif i == 0 :
c [ dex ] -= 1
elif i == 4 :
c [ dex ] = c [ dex ] - c [ dex + 1 ] + 70
else :
c [ dex ] = c [ dex ] + c [ dex + 1 ] - 70
print ( flag[::-1] )