REVERSE
Reverse-签到
flag:flag{94207979239367868421}
go语言逆向,非常难看,但是可以通过encrypt函数发现map映射,推测是字符映射加密
将local.txt替换为32-125的adcaii码,得到映射
0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyz{|}~
0690123456:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`dbcdejihijkmmnopqrstuvwxyzz|{~
由于6和0映射两个字符,使用递归爆破flag
def replace_and_generate(s, index=0, current_string=""):
if index == len(s):
# 如果到达字符串末尾,打印当前生成的字符串
print(current_string)
return
# 获取当前位置的字符
char = s[index]
if char == '6':
# 如果字符是'6',尝试替换为'9'和'1',并递归
replace_and_generate(s, index + 1, current_string + '9')
replace_and_generate(s, index + 1, current_string + '1')
elif char == '0' :
# 如果字符是'0',尝试替换为'0'和'3',并递归
replace_and_generate(s, index + 1, current_string + '0')
replace_and_generate(s, index + 1, current_string + '3')
else:
# 如果不是,保持字符不变,并递归
replace_and_generate(s, index + 1, current_string + char)
# 调用函数,输入原始字符串
replace_and_generate("flag{642076762360?78?8426}")
p = '''
flag{942079792390?78?8429}
flag{942079792390?78?8421}
flag{942079792393?78?8429}
flag{942079792393?78?8421}
flag{942079792310?78?8429}
flag{942079792310?78?8421}
flag{942079792313?78?8429}
flag{942079792313?78?8421}
flag{942079712390?78?8429}
flag{942079712390?78?8421}
flag{942079712393?78?8429}
flag{942079712393?78?8421}
flag{942079712310?78?8429}
flag{942079712310?78?8421}
flag{942079712313?78?8429}
flag{942079712313?78?8421}
flag{942071792390?78?8429}
flag{942071792390?78?8421}
flag{942071792393?78?8429}
flag{942071792393?78?8421}
flag{942071792310?78?8429}
flag{942071792310?78?8421}
flag{942071792313?78?8429}
flag{942071792313?78?8421}
flag{942071712390?78?8429}
flag{942071712390?78?8421}
flag{942071712393?78?8429}
flag{942071712393?78?8421}
flag{942071712310?78?8429}
flag{942071712310?78?8421}
flag{942071712313?78?8429}
flag{942071712313?78?8421}
flag{942379792390?78?8429}
flag{942379792390?78?8421}
flag{942379792393?78?8429}
flag{942379792393?78?8421}
flag{942379792310?78?8429}
flag{942379792310?78?8421}
flag{942379792313?78?8429}
flag{942379792313?78?8421}
flag{942379712390?78?8429}
flag{942379712390?78?8421}
flag{942379712393?78?8429}
flag{942379712393?78?8421}
flag{942379712310?78?8429}
flag{942379712310?78?8421}
flag{942379712313?78?8429}
flag{942379712313?78?8421}
flag{942371792390?78?8429}
flag{942371792390?78?8421}
flag{942371792393?78?8429}
flag{942371792393?78?8421}
flag{942371792310?78?8429}
flag{942371792310?78?8421}
flag{942371792313?78?8429}
flag{942371792313?78?8421}
flag{942371712390?78?8429}
flag{942371712390?78?8421}
flag{942371712393?78?8429}
flag{942371712393?78?8421}
flag{942371712310?78?8429}
flag{942371712310?78?8421}
flag{942371712313?78?8429}
flag{942371712313?78?8421}
flag{142079792390?78?8429}
flag{142079792390?78?8421}
flag{142079792393?78?8429}
flag{142079792393?78?8421}
flag{142079792310?78?8429}
flag{142079792310?78?8421}
flag{142079792313?78?8429}
flag{142079792313?78?8421}
flag{142079712390?78?8429}
flag{142079712390?78?8421}
flag{142079712393?78?8429}
flag{142079712393?78?8421}
flag{142079712310?78?8429}
flag{142079712310?78?8421}
flag{142079712313?78?8429}
flag{142079712313?78?8421}
flag{142071792390?78?8429}
flag{142071792390?78?8421}
flag{142071792393?78?8429}
flag{142071792393?78?8421}
flag{142071792310?78?8429}
flag{142071792310?78?8421}
flag{142071792313?78?8429}
flag{142071792313?78?8421}
flag{142071712390?78?8429}
flag{142071712390?78?8421}
flag{142071712393?78?8429}
flag{142071712393?78?8421}
flag{142071712310?78?8429}
flag{142071712310?78?8421}
flag{142071712313?78?8429}
flag{142071712313?78?8421}
flag{142379792390?78?8429}
flag{142379792390?78?8421}
flag{142379792393?78?8429}
flag{142379792393?78?8421}
flag{142379792310?78?8429}
flag{142379792310?78?8421}
flag{142379792313?78?8429}
flag{142379792313?78?8421}
flag{142379712390?78?8429}
flag{142379712390?78?8421}
flag{142379712393?78?8429}
flag{142379712393?78?8421}
flag{142379712310?78?8429}
flag{142379712310?78?8421}
flag{142379712313?78?8429}
flag{142379712313?78?8421}
flag{142371792390?78?8429}
flag{142371792390?78?8421}
flag{142371792393?78?8429}
flag{142371792393?78?8421}
flag{142371792310?78?8429}
flag{142371792310?78?8421}
flag{142371792313?78?8429}
flag{142371792313?78?8421}
flag{142371712390?78?8429}
flag{142371712390?78?8421}
flag{142371712393?78?8429}
flag{142371712393?78?8421}
flag{142371712310?78?8429}
flag{142371712310?78?8421}
flag{142371712313?78?8429}
flag{142371712313?78?8421}
'''
for i in p :
if i == '?' :
print ( '6', end = '')
else :
print ( i , end = '' )
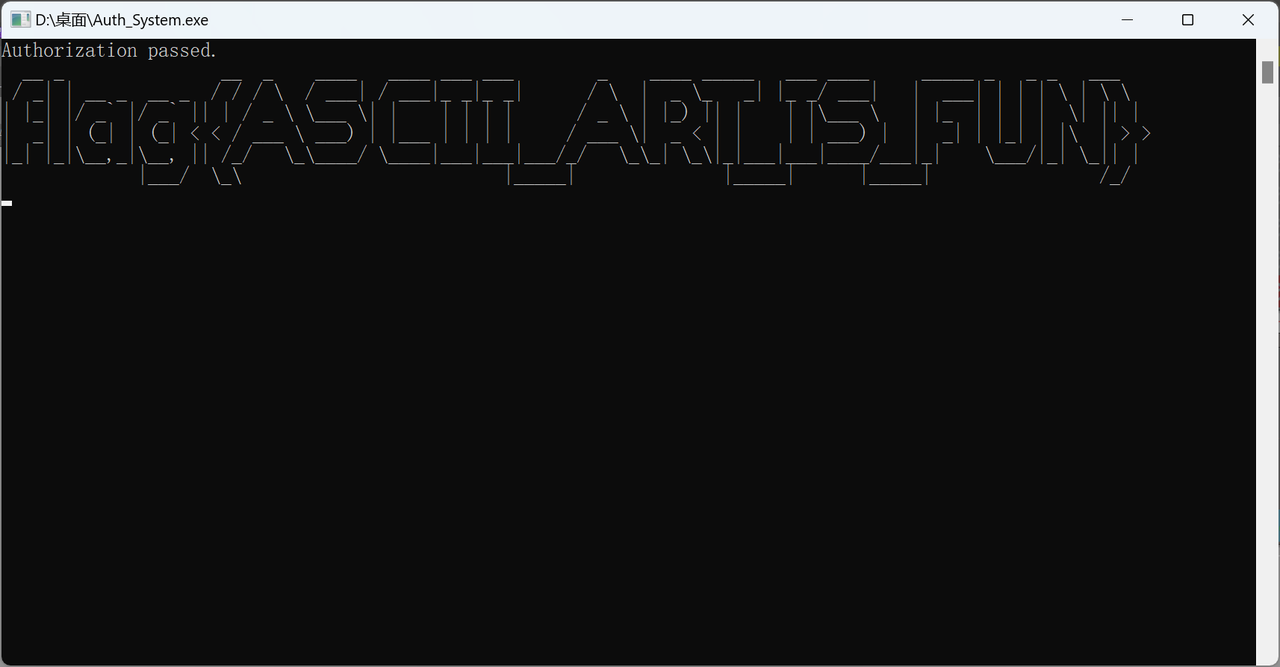
Auth System
flag:flag{ASCII_ART_IS_FUN}
64位exe,伪C代码没有东西,藏在汇编里
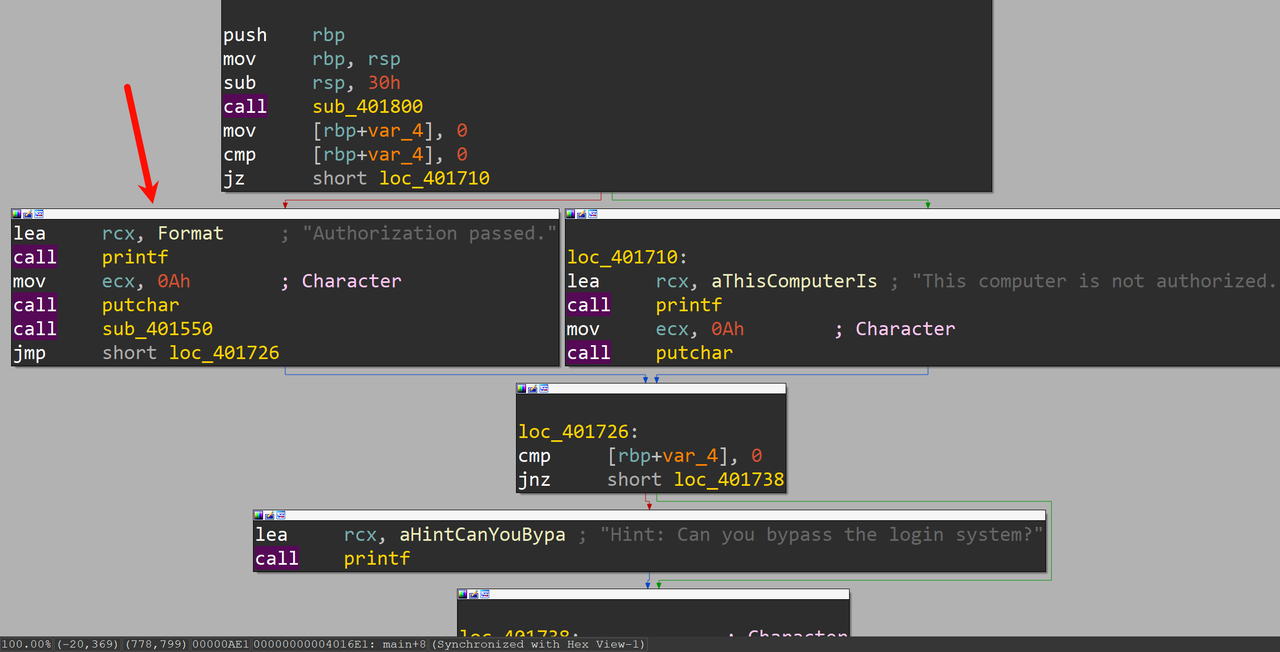
动态调试调至左侧即可打印出flag
MISC
Misc-签到
flag:flag{TreJaiuLT1rgbdfG0Eay}
10进制转字符
cipher = '''27880
30693
25915
21892
38450
23454
39564
23460
21457
36865
112
108
98
99
116
102
33719
21462
21069
27573
102
108
97
103
20851
27880
79
110
101
45
70
111
120
23433
20840
22242
38431
22238
22797
112
108
98
99
116
102
33719
21462
21518
27573
102
108
97
103'''
p = list ( cipher.split('\n') )
for i in p :
i = int ( i )
print ( chr ( i ) , end = '' )
注知攻善防实验室发送plbctf获取前段flag关注One-Fox安全团队回复plbctf获取后段flag
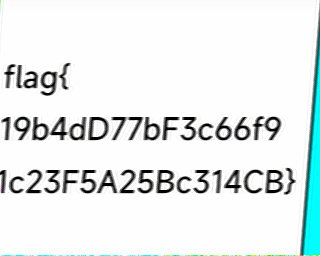
FM 145.8
flag:flag{19b4dD77bF3c66f91c23F5A25Bc314CB}
MMSSTV,装了虚拟声卡,跑的就是清晰!
江
百度识图 + 高德地图 == 湖北省武汉市江汉二路与江汉步行街交叉路口
ez_misc
flag:flag{b220116fc6ca827ecf3cb6c6c06dac26}
zip伪加密,获得一个jpg图片和一个加密rar压缩包
jpg末尾有提示this is password,后续跟着09 20的字节,推测snow隐写
snow.exe -C 1.txt
得到解压密码Carefree and carefree
CRYPTO
Crypto-签到
flag:flag{20df8477-faa1-45be-84c2-815896f57ea7}
RSA,给了n、p、c、e,发现n为平方数,修改一下欧拉函数即可
import libnum
import gmpy2
c = 82842906788636592492271066893769571955229168017356079088572626204245295058852564113933797086860938577522204614747010349961773519578853600805432478265574887247097136215988763430249336641865255009225100260144137595185775324909903020445877058452913281722437086851805024078007271164163452599950032199446517886066
p = 12997903135943019350944748082754549358026456093276038127266042371313868362099170139764055205606000548781749184149029011781127853420478548971045742939648447
e = 65537
n = 168945485931357376581910098129497447019127053765631385447420056057443645668530839223054528228945913700397201460738498087720357309974135107530141616346740842663335124641180686024764850956739174661813413634852386200714267489586995144627145935034041947210432347765428327462946968407678131243723755464551949511809
q = n // p
phi_n=p**2-p
#求逆元
d=libnum.invmod(e,phi_n)
m=pow(c,d,n)
print(m)
#数字转字节,转字符串
print(libnum.n2s(m).decode())